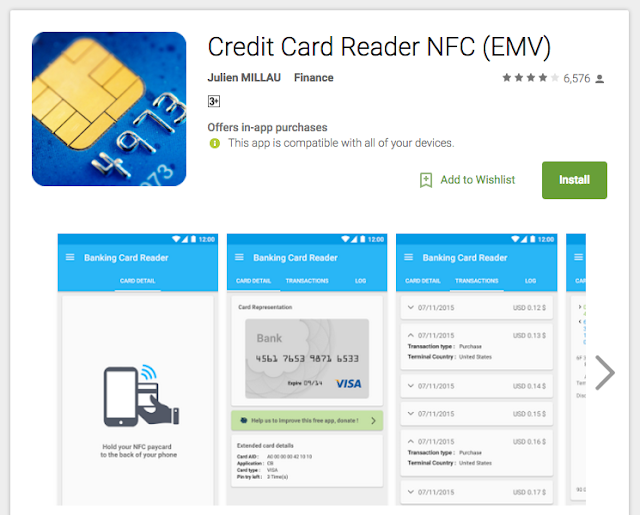
While browsing a presentation on hacking RFID devices, I realised just how easy it is to swipe a person's credit card information. All I had to do was to download and install the following app which is publicly available on the Google Play store:
Then, I activated the NFC capability on my smartphone and put it on top of my wallet where my debit card is kept. To my horror, my card details started appearing on my phone.
First and most importantly, it has my credit card number which is technically the only piece of information that is needed to make a purchase. A simple Google search will show you the way to many merchants that will allow you to exploit a credit card number even without the CVV/CVC code. That being said, it's still not difficult to bruteforce a 3-digit (1000 possibilities) CVV/CVC.
Aside from that, it also has the expiry date of my card, the name of the bank that issued my card and the type of my card (debit/credit). On some cards, it may even be able to retrieve your full name but that is not strictly required for a fraudster to make purchases using your card. On another tab, it showed me the transactions that I made using this card. For each transaction, it logged the date, the amount and the currency in which the transaction was made. Put together, I can imagine many uses of these information for a criminal:
So what may be a solution to this madness? Well, one way might be to not let anybody close to your card, but given that one may amplify the reading strength of the reader (some sources say up to 1.5m), this is not really a foolproof solution. So maybe you decide to buy a RFID blocking wallet. But what if (and I know this is slightly far-fetched) criminals start putting up spoofed readers, making you think it's actually safe to tap on them?
In my opinion, a real fix can only be made by a redesign of the EMV. Firstly, information on the card shouldn't be freely accessible to anyone who requests to read it. Secondly, the data transmitted by the protocol should be encrypted to prevent sniffing. Last but not least, there should be some mechanism to ensure session integrity so that an attacker is not able to inject rogue commands into a legitimate session.
In the meantime, just wrap your card in an aluminium foil :P
Then, I activated the NFC capability on my smartphone and put it on top of my wallet where my debit card is kept. To my horror, my card details started appearing on my phone.
First and most importantly, it has my credit card number which is technically the only piece of information that is needed to make a purchase. A simple Google search will show you the way to many merchants that will allow you to exploit a credit card number even without the CVV/CVC code. That being said, it's still not difficult to bruteforce a 3-digit (1000 possibilities) CVV/CVC.
Aside from that, it also has the expiry date of my card, the name of the bank that issued my card and the type of my card (debit/credit). On some cards, it may even be able to retrieve your full name but that is not strictly required for a fraudster to make purchases using your card. On another tab, it showed me the transactions that I made using this card. For each transaction, it logged the date, the amount and the currency in which the transaction was made. Put together, I can imagine many uses of these information for a criminal:
- Make fraudulent purchases using your credit/debit card (online or magnetic stripe card clone)
- Lock you out of your card by sending more than 3 PIN attempts to your card
- Profile you for social engineering/phishing attacks
So what may be a solution to this madness? Well, one way might be to not let anybody close to your card, but given that one may amplify the reading strength of the reader (some sources say up to 1.5m), this is not really a foolproof solution. So maybe you decide to buy a RFID blocking wallet. But what if (and I know this is slightly far-fetched) criminals start putting up spoofed readers, making you think it's actually safe to tap on them?
In my opinion, a real fix can only be made by a redesign of the EMV. Firstly, information on the card shouldn't be freely accessible to anyone who requests to read it. Secondly, the data transmitted by the protocol should be encrypted to prevent sniffing. Last but not least, there should be some mechanism to ensure session integrity so that an attacker is not able to inject rogue commands into a legitimate session.
In the meantime, just wrap your card in an aluminium foil :P




Comments
Post a Comment