Stage 1 - The Downloader
1.1 Classification
The sample is a word document from a recent spam campaign. First, I submitted the sample to VirusTotal to see if there is existing information about the behaviour of the malware. It turns out there is and most anti-viruses have classified it as a downloader. A downloader is usually a malware that downloads other malicious payloads onto the victim computer. Also, we note that the MD5 hash of the file is 9e23af4b5bef43147b28ccfb350a8a56. This information might be useful for anti-viruses that rely on simple signature detection.1.2 File Name & Creation Date
Based on various reports, I noticed a pattern in the filename, "Subpoena %NAME%.doc" where %NAME% might be substituted with any name (e.g. Steve Raguz, Jim Martner). We may also guess from the metadata of the file that the document was created on 27 April 2016. Based on this, we will realise later on that this malware actually has a very short lifespan (around 4 days). |
| We can see the original file name and classifications from various anti-virus vendors on VirusTotal |
1.3 Social Engineering Technique
Since it is a Word document, I am guessing that there might be embedded VBA macros and indeed, the VirusTotal report confirms this. However, let's first take a look at how the attacker tricks the victim into enabling these malicious macros: |
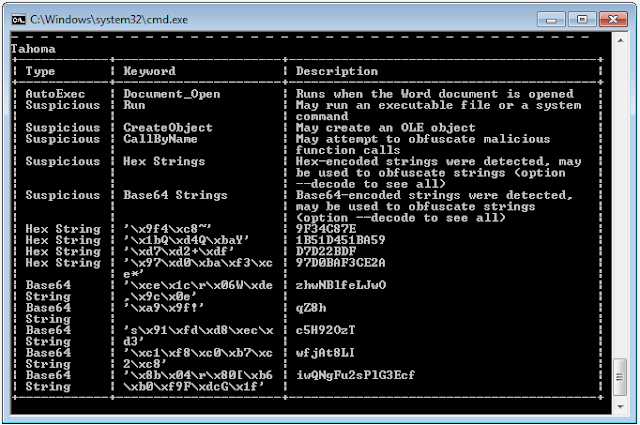
1.4 Extracting the VBA Macros
Now let's see what macros are embedded within the document. For this, I will be using OleVBA to perform the analysis and extraction of the macros. Running olevba.py malware.doc, I get:As expected, the macros have the ability to automatically execute once they are enabled. It also seems to have the ability to execute a file or system command. Let's now extract the VBA scripts (I used OfficeMalScanner to do this):
1.5 Analysis of the VBA Scripts
Evidently, execution starts in the Document_Open() event procedure that is automatically executed when the document opens (and the macros enabled).However, since the VBA code is heavily obfuscated, I had to resort to debugging and deobfuscation in order to fully understand the code.
1.5.1 Anti-Analysis Techniques
The first interesting piece of code is here, where they check if the username is equal to "USER" and if the machine name is equal to "HOST". If this is true, then the malware would later hide its behaviour.The next anti-analysis branch takes place here:
In this case, if the manufacturer name or model of your machine contains any of the blacklisted strings (case-insensitive), then the malicious script will also be alerted and suppress its behaviour later on. The list of blacklisted strings are: "KVM", "QEMU", "RED HAT", "VIRTUAL", "VMWARE" and "XEN". Of course, such a paranoid process would also check the process list to see if any of them are blacklisted too:
In this script, it checks if any of the process names contain the following case-insensitive substrings: "FIDDLER", "PROCEXP", "PROCMON", "SNORT", "SURICATA" and "WIRESHARK".
Finally, the script checks the path of the document directory to see if it contains the substring "1461771256_us". If it does, then the malware is allowed to run. Otherwise, if any of the tripwires were activated earlier, then it will simply quit. The latter check might have been used by the malware author to test and debug his script (or we can also cook up some conspiracy theory).
1.5.2 Malicious Behaviour
Now, let's see what the malicious script does if it had passed all the checks before:
- Firstly, the downloader sends a GET request to the url hxxp://chienenforme.com/img/doc.exe.
- Then, it checks the status of the response to ensure that the status code is 200 (OK).
- Following which, it extracts the response body (the malicious binary)
- It then generates a random path in the user's %TEMP% directory for storage of the malicious binary. The file name of the malicious binary is generated randomly (e.g. 0.7055475). Hence, the final path of the malicious binary is "%TEMP%\RND_FLOAT".
- Finally, the downloader executes the malicious binary.
In my next post, I will continue with my findings on the malicious binary.






Comments
Post a Comment